Generate RSA keys with SSH by using PuTTYgen
One effective way of securing SSH access to your cloud server is to usea public-private key pair. This means that a public key is placed onthe server and a private key is placed on your local workstation.Using a key pair makes it impossible for someone to log in by using justa password, as long as you set up SSH to deny password-basedauthentication.

This article provides steps for generating RSA keys by using PuTTYgen onWindows for secure SSH authentication with OpenSSH.
Generate keys
In Windows, use PuTTYgen to generate your public and private keys.
- If needed, download PuTTYgen from the PuTTY download page.(PuTTYgen might have been installed previously with PuTTY or WinSCP.)
- Launch the program, and then click the Generate button.The program generates the keys for you.
- Enter a unique key passphrase in the Key passphrase andConfirm passphrase fields.For additional information about using passphrases,see Log in with a SSH Private Key on Windows.
- Save the public and private keys by clicking the Save public keyand Save private key buttons.
- From the Public key for pasting into OpenSSH authorized_keys filefield at the top of the window, copy all the text (starting with ssh-rsa)to your clipboard by pressing Ctrl-C.You need this key available on your clipboard to paste eitherinto the public key tool in the Control Panel or directly into theauthorized keys on your cloud server.
Use the key pair

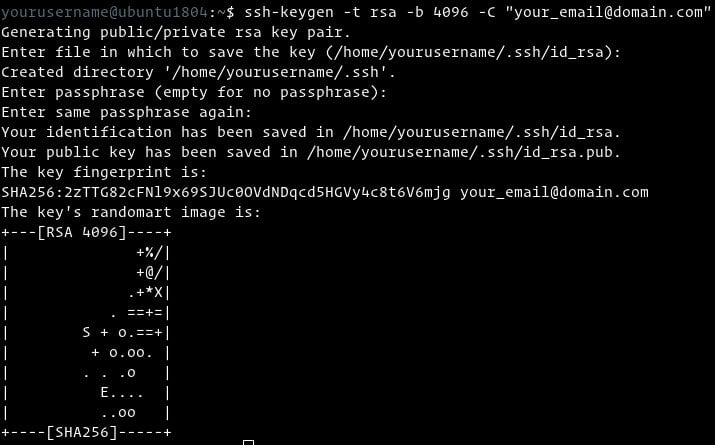
Generating a new SSH key. Open Terminal Terminal Git Bash the terminal. Paste the text below, substituting in your GitHub Enterprise email address. $ ssh-keygen -t rsa -b 4096 -C 'youremail@example.com' This creates a new ssh key, using the provided email as a label. Generating public/private rsa key pair. There is already a command in the ssh suite to do this automatically for you. I.e log into a remote host and add the public key to that computers authorizedkeys file. Ssh-copy-id -i /path/to/key/file user@host.com If the key you are installing is /.ssh/idrsa then you can even drop the -i flag completely. Much better than manually doing it! Ssh-add /.ssh/idrsa The private key passphrase is now stored in ssh-agent. Use ssh-copy-id to copy the key to an existing VM. If you have already created a VM, you can install the new SSH public key to your Linux VM with a command similar to the following: ssh-copy-id -i /.ssh/idrsa.pub azureuser@myserver Create and configure an SSH config file.
You can use the RSA key pair in the following ways.
Specify your SSH key when creating a new cloud server
When you create a cloud server, you can assign a public key from the list of keys.If your key is not already in the list, you may add it, and then assign it.
Add a new public key to the list
- Under Advanced Options on the Create Server page, click Manage SSHKeys.
- Select public key for the cloud server from the SSH Keys listand click Add Public Key.
- Enter the key name, select the region, and paste the entire publickey into the Public Key field. Then click Add Public Key.
- Go back to the Create Server page, and confirm that your key is listedin the SSH Key list.
Assign a public key
- Under Advanced Options on the Create Server page, select the publickey you want to use from the SSH key drop-down menu.
- When you are done specifying the all the other details for the server,click Create Server.
Assign your SSH Key to an existing cloud server
To make use of your newly generated RSA key pair, you must tell PuTTY touse it when connecting to your cloud server.
To edit the file (or create it), run the following command on the cloud server:
Paste the text onto its own line in the file.
You must have the key available in your clipboard to paste it. The key and itsassociated text (the ssh-rsa identified at the start and the comment at the end)must be on one line in the file. If the text is word-wrapped onto multiple linesan error might occur when connecting.
If you created the authorized_keys file, change its permissionsafter you’re done editing it by running the following command:
Open PuTTY, and go to the SSH > Auth section.
Browse to the location of the key file, and load the private key.
Go to the Session page, and save the session. This saves the configurationso that PuTTY uses the key every time that you connect to your cloudserver.
After you save your session, your key is loaded automatically when youconnect to your server.
Generate New Rsa Key Ubuntu 2017
Related article
Experience what Rackspace has to offer.
©2020 Rackspace US, Inc.
Except where otherwise noted, content on this site is licensed under a Creative Commons Attribution-NonCommercial-NoDerivs 3.0 Unported License
SSH is a cryptographic network protocol which is used to securely connect to a host over an unsecured connection. By default, any Linux operating system supports SSH; hence using a third party client is unnecessary like in the Windows platform. SSH protocol requires a server which accepts SSH connections, and a client which sends the requests to connect to the host. The typical usage of SSH protocol is remote login, remote commanding, and file transfer. Nowadays many Linux based servers make use of SSH protocol to tighten its security. A notable part of the SSH protocol is its authentication key pair which is used to identify and authorize users. So, this article demonstrates what are they, how to generate them, and how to utilize them to protect the server, and other relevant information.How to Generate Keys and What Are They?
Generating SSH key pair consists of two basic phases. The first phase is generating the key pair on the local side, the second phase is copying it to the remote host, registering in the server and configuring the ssh daemon to make it useful. A key pair consists of two files, id_rsa and id_rsa.pub which are private and public keys respectively. The public key resides on the server side, whereas the private key is used when accessing it over SSH protocol.
In the following example ssh-keygen command is used to generate the key pair. When generating the key pair, the command prompt asks a name for a key, if it’s omitted the default name – id_rsa is used instead.
How to Use the Keys?
Once the key pair is generated on the local side through terminal window, the next step is to prepare them for employing for authentication purpose. The most convenient way to upload and register the public key in the server is using the ssh-copy-id command, what it does is copy the public key to the given user account located in the given host. As seen in the following example when the ssh-copy-id, username, the host name along with the password are all given the public key is copied and registered on the server side. If the username is root, the public key is uploaded to /root/.ssh/ on the server.
That being said, the server still isn’t protected with the SSH key pair as it’s not configured properly. Anyone can still access to the server if the password of the user account is known; hence the password has to be disabled while enabling the key pair verification. To disable the password authentication, edit /etc/ssh/sshd_config file where the settings for the SSH daemon are contained. In the file, the PasswordAuthentication has to be altered to NO, ChallengeResponseAuthentication should be altered to No as well. As the next step the sshd daemon has to be restarted for changes to take effect, which can be done with sudo systemctl reload sshd. Finally, the new key pair authentication method can be tested by giving ssh username@username in the terminal window.
Theory of The Keys and How They Work
The key pair is a part of the SSH standard which is used to connect to a remote host over an unsecured network. As stated earlier, the key pair consists of two keys – public and private keys which are uploaded to the server side and kept on the client side respectively. The public key is denoted by .pub extension, and the private key doesn’t have any extension.
When the user is accessing the server, the SSH daemon installed on the server side requests the user for the SSH private key, if it’s provided the private key is compared against the public key in the server. If the private key corresponds to the public key, authentication is successful, otherwise it rejects the login request. By default, the key pair uses RSA which is a cryptographic algorithm to generate the keys. But there are other popular algorithms as well, such as DSA and ECDSA.
ssh-keygen Command Line Options
ssh-keygen is used to generate keys and it provides a number of options to ease the key pair management, tighten the security and increase the flexibility. The following options are some of the prominent options which may come handy when managing a server.
Passphrase
Ssh Rsa Key
The Passphrase option is used to provide a secondary protection when a key pair is used to authenticate the user. What it does is to secure the private key with a password and consequently the user is required to provide the passphrase when logging in to the remote host. It asks during the key pair creation.
Generate New Rsa Key Ubuntu Download
Change the Bit Strength
Bit strength refers to the key pair’s key size which defines how strong the key pair is. Nowadays the standard size is 2048 bits, but it used to be 1024 bits and is no longer acceptable as it’s speculated that many powerful hardware are capable of cracking anything up to 1024 bits or even above given the right amount of time. Fortunately, ssh-keygen currently supports higher bit strength values such as 2048 and its next fashionable number 4096 which is recommended if it’s possible due to the large bit strength. The bit strength value can be adjusted with –b command, if it’s omitted the default value – 1024 or 2048 depending on the ssh-keygen is used.
Rsa Key Generation Program
Comment Public Key
Commenting is applicable to the public key, and is useful in organizing the keys if there are a large number of keys involved. The typical usage of commenting is when multiple admins use a server, but still want to distinguish one key from another. The following format is used to add a comment when generating a key pair.
Change Passphrase of a Private Key
Like adding a passphrase when generating a key pair, the existing passphrase can also be changed. Since the passphrase is applicable to the private key which resides on the client side, the command has to be executed on the client side along with the name of the private key. This option takes 3 parameters, old password, new password and the private key to apply the changes.
Change the Cryptographic Algorithm
The Algorithm defines how the information in the key pair is encrypted in order to verify each other when the connection is being established. Ssh-keygen supports several popular algorithm types which are RSA, ECDSA, DSA, ED25519 and RSA1. Nowadays the popular algorithm among many servers is RSA due to its wide spread usage and relatively good security, however it’s currently being upgraded to the newer version ECDSA which is much lighter, and has a low bit value with a high security compared to RSA. ED25519 is the newest version among these, and therefore not many clients support it, but still server side implementation is possible at the moment. DSA is the oldest version among all these algorithms, and is no longer employed in most of the hosts as it’s not secure anymore. According to OpenSSH 7 standard the support for DSA will no longer be given. The format to use the algorithm is as following.